Introduction
Regulators have raised their scrutiny of critical vendor relationships involving sensitive data. The current FDIC Compliance Examination Manual has 104 items listed for review to evaluate how well an institution manages its vendor-related risk. The regulatory emphasis on this risk is understandable, as it includes all risks an institution faces directly placed into an environment outside of its direct control.
This has shifted the paradigm of vendor management programs toward more thorough selection processes and more effective oversight.
A strong vendor management program involves five core principles, which are derived from expectations put forward by the regulators. This article will provide guidance on how to form a strong vendor management program that meets regulatory requirements and provides a long-term benefit to the institution.
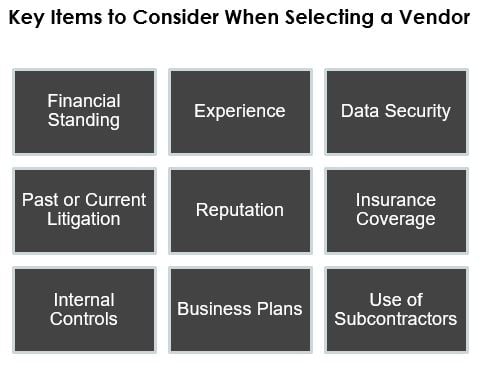
Risk Assessment and Due Diligence: Find the Right Vendor
The vendor selection process should begin with a comprehensive risk assessment and cost-benefit analysis. First, this will help the institution to determine if its best option is to outsource the function or to retain it in-house. Second, if the function will be outsourced, this will provide essential guidelines for selecting the right vendor, as well as the framework for how that vendor’s performance can be evaluated.
Getting the necessary expertise involved is essential at this stage. It should include executive guidance along with insight from departments that will be relying most directly on the vendor relationship. This brings key perspectives into considering risks and benefits, and in the process of deciding which potential vendors are the best fit for the institution. In addition, throughout the vendor management program, there should be executive communication and accountability that still includes experienced voices from the individual departments involved in the vendor relationship.
Structuring the Contract: Keep Your Institution Protected
The contract is the element that will protect the interests of the institution and provide the necessary guarantees to meet its needs in a consistent and timely manner.
It is important, therefore, to ensure that all expectations are clearly defined. Scope of work requirements need to include standards of quality, timeliness, and security that will keep the institution is adequately protected.
Most importantly of all, ensure that any contracts will align your vendor with the goals and objective requirements for the functions being outsourced.
The vendor should continue to earn your business, even after the contract has been signed. As such, the length of the contract, the service requirements, and the processes for addressing any problems must be given careful consideration.
One important issue that is often overlooked in a contract is the procedure for unwinding the relationship when the contract expires or is terminated. A clearly defined statement of work should be added to the contract that includes timeliness, data recovery and other intellectual property procedural issues that will be needed as you transition away from the vendor.
Federal regulators who are reviewing contracts you have with critical vendors will be looking for answers to the seven contract requirements shown in the attached graphic.

Assess Internal Performance and Controls: Maintain Standards
Even the best-formed contracts are still words in a document. Appropriate reporting and audits should be part of the agreement and reviewed regularly.
Because a business interruption could have severe consequences on your institution, you need to periodically review the policies and procedures of your third party vendor. Many lenders review the documentation shown in the graphic on an annual basis.
Vendor management best practices trend each one of these policies and procedures. Trending looks for annual improvements denoted in the reports. Is the vendor improving its policies and procedures on an annual basis? Is the vendor expanding their SOC audits to other areas of their company? Improvement or expansion of the scope of any of these documents is a good sign that your vendor is improving. If documents the same year over year, is the vendor only using them to pass initial due diligence?
Activity reports and audit reports must have enough information to establish if your needs and goals are well served. Through their policies and audit reports, your vendors should be able to demonstrate that they have adequate controls in place to maintain the necessary service levels.
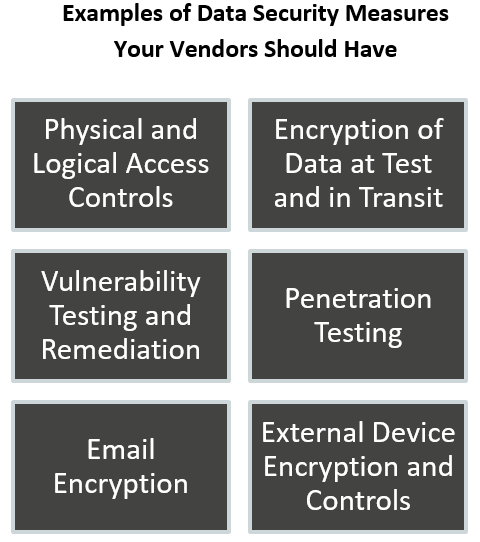
Check Data Security Measures: Ensure Sensitive Data Stays Safe
The security of your customers’ sensitive data needs to be given special attention. The rapid rise in our use of the Internet to perform daily activities in business and in our personal lives has made data security efforts more imperative than ever. Regulators have responded with particularly heavy scrutiny toward the cybersecurity and the methods institutions and their vendors use to maintain data security.
Broadly speaking, there are two ways in which sensitive data can be exposed: procedural failures and technological failures. Procedural failures occur through human error, either as a result of poorly designed policies or simply not adhering to policies. This further illustrates the necessity for careful review of a vendor’s policies and procedures and for clear, readily accessible means of oversight.
Technological failures occur when software or equipment meant to ensure that sensitive data is kept secure somehow fails to do so. There are strong links between procedural and technological requirements, however, and one may proceed from the other. This is particularly true if a vendor does not have sufficient technological capacity to maintain the necessary levels of security. Therefore, a careful review of what kind of security technology is being used by a vendor is essential.
Understand the Vendor’s Business Plans and Goals: Have an Eye on the Future
When considering a relationship with a vendor, whether a new vendor or one with which your institution has an ongoing arrangement, there is a lot of information to consider to ensure present needs are met. It is equally important to consider how well that vendor will be able to continue meeting the needs of the institution in the future.
The regulators offer some key points to consider for determining if a vendor is likely to provide service in a timely and effective manner even as needs grow and evolve. These points are summarized in the table. The regulators effectively hold the institutions they oversee solely responsible for making this determination.
To make the most of your vendor management program, therefore, consider finding vendors who view themselves as a partner in that program.
Ideally, your vendor will monitor and respond to significant changes in the law, regulations, technology, or any other element that may impact the functions for which it is responsible. Together with effective oversight, this enables your institution to have confidence that the vendor is actively looking out for your best interests and the interests of your customers.

Conclusion
Having a vendor management program is a necessity for all institutions, but it is extraordinarily important to ensure it is well-designed.
A poorly designed program may even become a risk unto itself, as problems may go unnoticed with breakdowns in communication and oversight over key areas.
A well-designed program, however, will do more than just meet regulatory requirements. It will enable your institution to measure the full value of its vendor relationships and ensure it is always prepared to offer the best services to its customers.
Miniter’s Force-Placed Insurance Program and VSI Insurance Claims process involve enhanced vendor management scrutiny due to these systems holding borrower personal information.
Would you like to be invited to our complimentary webinars? Subscribe here.

